In the recent few articles, we have installed the OpenSSH server, and now we will see how to secure OpenSSH Server in Linux.
Already you know the SSH server is the best secure and simple, and easy way to connect with the remote servers, router, and switches. Using OpenSSH gives you one more layer of security.
We just had to do a basic set up at the installation time, but you need to tweak more to get a highly secure way to connect.
Few tweaks are required to harden security. So, you need to follow me and change or update the setting according to your need.
How to achieve a high secure OpenSSH server?
At the time of accessing a remote server, it requires authentication. We provide the password which we had created at the time of installation.
In this scenario, an evil guy will make some guess or brute force to gain access to your servers, and actually, this type of password can be easily gained by an evil guy.
So, you are thinking about what to do now? Take a sigh of relief. Thanks to the community, we have the option to set up SSH as a passwordless Authentication.
1. What is OpenSSH Passwordless Authentication and How to setup?
In this public key, an OpenSSH passwordless is stored into a remote server and access the remote server private key is required by the client.
For example, When John wants to connect with his remote server through OpenSSH, the private key must set up the connection. If the private key matches with the server’s public key, then John gets permission to access his server, or else John will be kicked out.
I think this explanation gives you a clear idea and now we will create an SSH key-pair. First, we have to generate ssh key-pair.
ssh-keygen -f trendocan -t rsa -b 4096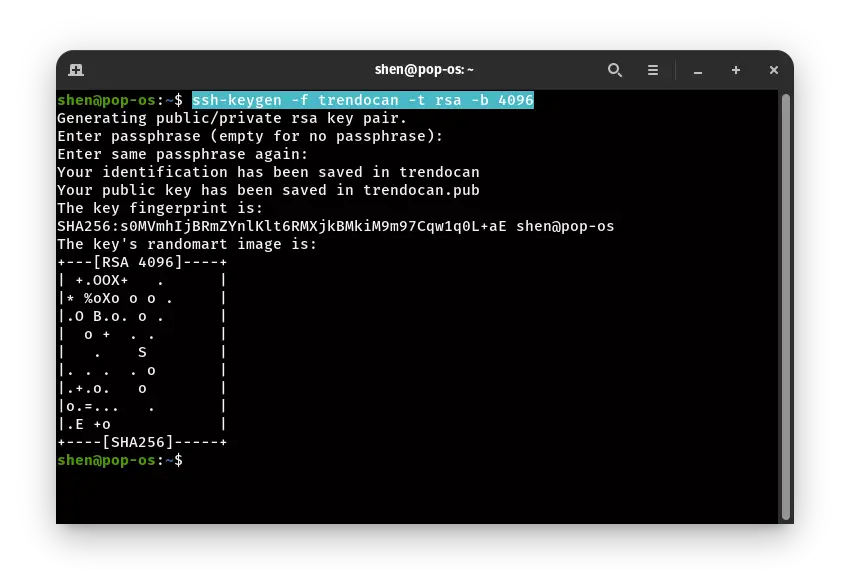
In the I have RSA encryption, you can use other encryption also, and to give the filename, you have to use the parameter -f and provide the filename.
After doing this step, you need to copy this public key to your server, and the private key will be stored in a host pc
One last step is required for passwordless Authentication. For this, you have to modify the SSH configuration file.
sudo nano /etc/ssh/sshd_configI have used a nano editor. You can use another editor as per your preference. In the editor, you need to uncomment PasswordAuthentication and change “yes” to “no,” or you can replace from below code
PasswordAuthentication no
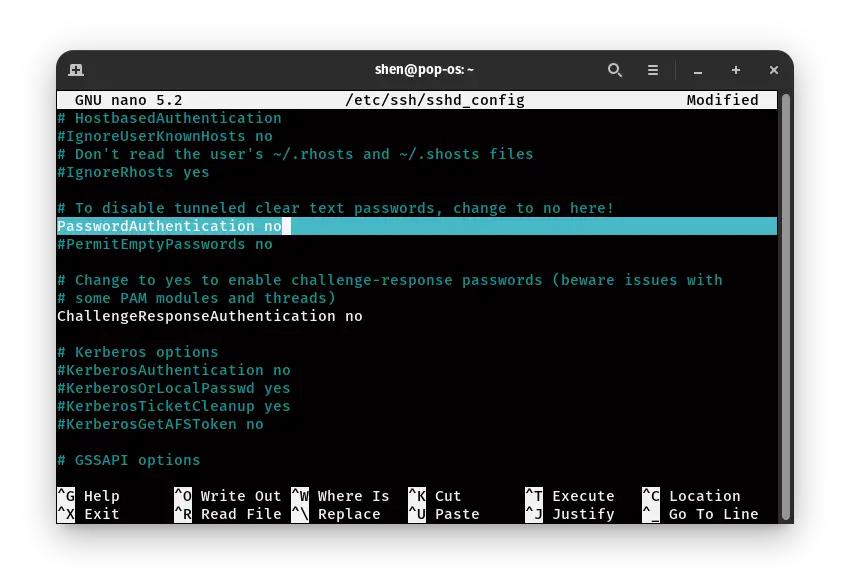
One thing is left before this make sure to save this file in the nano editor. To save the file, use Ctrl + O then Y, Now to restart the service. To restart the sshd service pass this command
sudo systemctl restart sshdThat’s it, Now the OpenSSH server will not ask password for login, and you are only left to connect to the server using SSH key authentication.
Read this: Latest:2020 How to Mount and Unmount File System in Linux?
2. How To Disable user SSH EmptyPassword connection?
In OpenSSH server has the option to grant users access to the system without providing any password or passphrase.
Why I’m telling you because sometimes administrator create the user account, but somehow they forgot to provide a security password
Some evil guy can take advantage to gain access using this method to kick out unknown authentication you need to disable the PermitEmptyPassword.
So, How to disable then? The simple you need to go the same configuration file you had access to a few seconds ago.
sudo nano /etc/ssh/sshd_config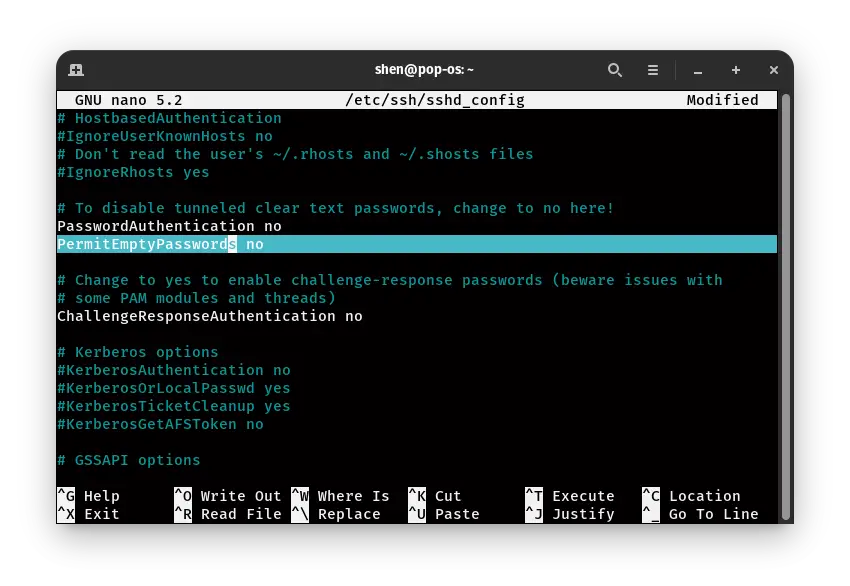
Find the PermitEmptyPassword then uncomment and change “yes” to “no”.
Next and last step is to restart SSH service.
$ sudo systemctl restart sshd3. How to Limit SSH Access to Specific Users?
OpenSSH provides several options to enhance security to protect from any breach.
Through this security mechanism, only specified users can access a remote server. No other user can get permission to log in and do any modifications.
Adding this security layer will reduce the chance of trespassing. To enable this feature, you have to open the same configuration file. /etc/ssh/sshd_config
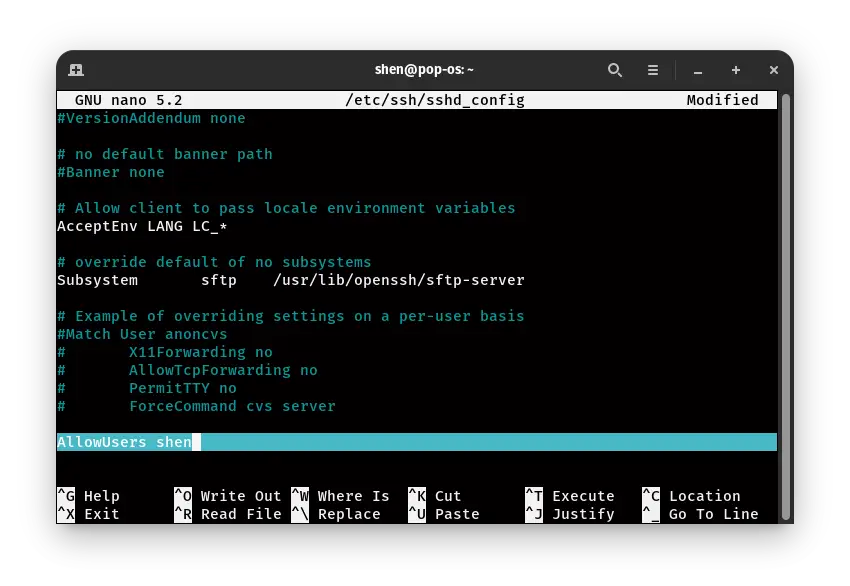
As per the above image, you need to add “AllowUsers” with the user’s name to whom you want to grant access.
AllowUsers shen
After that restart the “sshd” service to apply changes.
sudo systemctl restart sshd
Read this How to monitor file content while they change in Linux
4. How to set the number of Password Attempt in OpenSSH?
In the above method, you know how you can allow only a specific person, now. In this paragraph, you will add one more security layer through which the brute force method will not work.
In this method, we will set the maximum number of attempts to log in to a remote server.
As usual open, the configuration file and find “MaxAuthTries,” then change the number of auth as per your preference.
MaxAuthTries 3
In my case I have set max attempt 3
That’s it now restart the OpenSSH server using command
sudo systemctl restart sshd5. How to Disable SSH Root logins
When the evil guy somehow got access to your server, your system, user data, financial loss, or any bad situation can occur.
So, We will share the method through which you will disable the root permission to SSH users.
To proceed further you need to open the configuration file once again let you know the command
sudo nano /etc/ssh/sshd_configIn this configuration file you need to find PermitRootLogin by default it will be prohibit-password change it “no“
This will not allow root login through SSH, but If you require SSH, you can add users into the sudo group.
$ sudo systemctl restart sshd
How to change or use SSH Protocol 2?
There are two versions of SSH protocol: SSH Protocol 1 and SSH Protocol 2.In the SSH Protocol 1 has several vulnerabilities that can harm your system.
SSH Protocol comes with an advanced and more secure way to connect with a remote server, Features like a strong cryptographic check, Bulk encryption, and robust algorithm.
When you start using ssh, the pre-default version is SSH Protocol is 1.So; you need to change version 1 to 2.
I think so rest process you already know Open the SSH configuration file and add a line
Protocol 2
Now just close this nano editor after pressing “Ctrl + O” and “Y,” then restart the SSH server, passing the command
sudo systemctl restart sshdThat’s it now your SSH Protocol Version is 2.
Conclusions
Make sure to tweak the default setting to enhance security parameters. Otherwise, some evil guy will get access, and they will kick you from your server.
Many options are still left in SSH configuration to cover, which you can change like, IDLE Time, Grace Time, and many others.
Let me know if you are facing any issues during setup SSH Security. I’ll try to solve your issue.