Statistically, over 10% of users forget or lose their passwords or private keys for encrypted data.
This is not a big problem if there is a password or private key recovery option, but it becomes a disaster when there is no way to recover the lost or forgotten password or private key.
According to cryptocurrency data firm Chainalysis, over three million bitcoins are considered lost due to forgotten passwords.
Stefan Thomas, a San Francisco-based investor, became famous when he revealed that he lost his private key to the hardware-based crypto wallet IronKey, which holds 7,002 bitcoins. The value of this loss (in dollars) was $479,784,042 on November 5, 2021. The value of losses from lost private keys to encrypted data, files, drives is not possible to estimate accurately.
To avoid such disastrous situations, users may use a simple four-step approach to generate easily recoverable private keys based on dynamical passwords.
Table of Contents
What is Dynamical Passwords
Dynamical passwords are parametric, dynamic, recoverable, generated on demand, and pseudo-random passwords not stored in electronic or paper form.
The most crucial property of dynamical passwords is the easiness of recovery from some memorable parameters. The most common parameters are key and date (year, month, day). If, for example, you choose the name and birth date of one of your relatives, friends, or some famous persons, you will be able to recover the password with these parameters quickly.
This article teaches how to generate recoverable 256-bit private cryptographic keys for bitcoin wallets using public dynamical password generators (DPGs). Our approach consists of the following four steps:
- Define input parameters for the DPG.
- Get dynamical passwords via cURL’s POST requests to a public dynamical passwords generator (DPG).
- Select 32 symbols from the dynamical passwords.
- Convert 32 symbols into a 256-bit private cryptographic key.
A simple bash script
In this section, we describe a simple bash script, which performs the four steps required.
Step 1. Define parameters
key='test' day=2 month=2 year=2022
Step 2. Send a POST request with cURL to a public DPG
url='https://dynpass.online/dpt/dpt.php' curl -X POST -F 'key='$key -F 'day='$day -F 'month='$month -F 'year='$year $url > dp.tmp
As a result, we get 10 passwords with a length of 15 symbols, each saved in the file “dp.tmp”.
Step 3. Select 32 symbols from the dynamical passwords
out=$(awk '{if (NR<3) s=s $2;if (NR==3) s=s substr($2,1,2)} END {print s}' dp.tmp)
Step 4. Convert 32 symbols to the 256-bit binary number, which is the required private key
echo “Your private key:” echo $out |perl -lpe '$_=join " ", unpack"(B8)*"'
The listing below is the full bash script.
key='test'
day=2
month=2
year=2022
url='https://dynpass.online/dpt/dpt.php'
curl -X POST -F 'key='$key -F 'day='$day -F 'month='$month -F 'year='$year $url >dp.tmp
out=$(awk '{if (NR<3) s=s $2;if (NR==3) s=s substr($2,1,2)} END {print s}' dp.tmp)
echo “Your private key:”
echo $out |perl -lpe '$_=join " ", unpack"(B8)*"'
Create a file named “pk_basic.sh” and store the above script in this file.
Then give the executable permissions to this file with the following command.
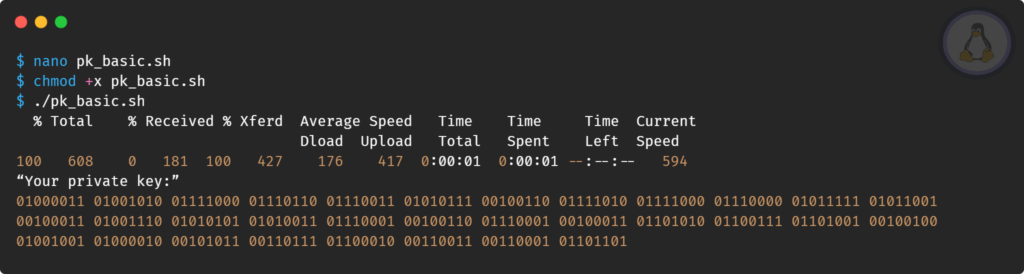
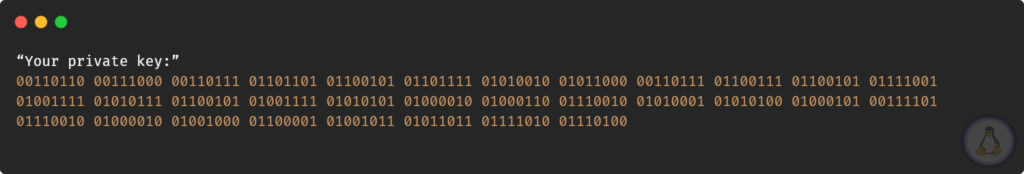
$ chmod +x pk_basic.shFinally, execute the script using the below command.
$ ./pk_basic.shThe picture below shows the behavior of this script.
Adding a simple user’s interface
Using echo and read commands, we can create a simple user interface as shown in the below script.
echo "Enter a key"
read key
echo "Enter a day"
read day
echo "Enter a month"
read month
echo "Enter an year"
read year
url='https://dynpass.online/dpt/dpt.php'
curl -X POST -F 'key='$key -F 'day='$day -F 'month='$month -F 'year='$year $url >dp.tmp
out=$(awk '{if (NR<3) s=s $2;if (NR==3) s=s substr($2,1,2)} END {print s}' dp.tmp)
echo “Your private key:”
echo $out |perl -lpe '$_=join " ", unpack"(B8)*"'
Now create a file named “pk_si.sh” and store the above script in this file.
Then give the executable permissions to this file with the following command.
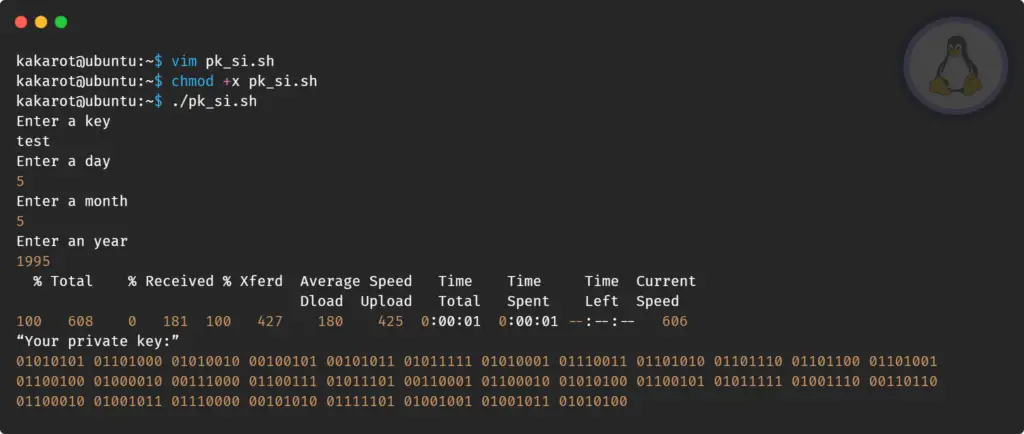
$ chmod +x pk_si.shFinally, execute the script using the below command.
$ ./pk_si.shThe picture below shows the behavior of this script.
Adding the dialog’s interface
We can create a better user interface using the dialog utility, as shown in the below script.
clear
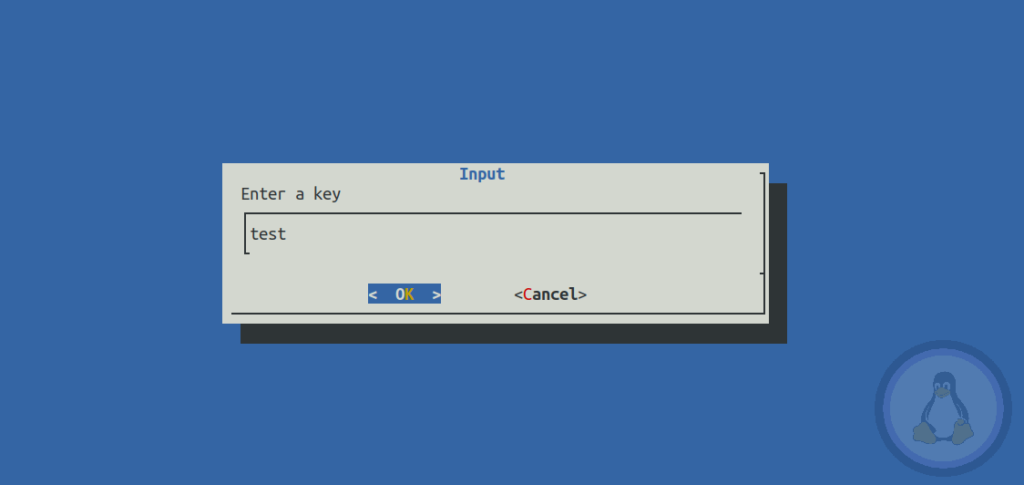
key=$(dialog --title "Input" --inputbox "Enter a key" 8 60 2 3>&1 1>&2 2>&3 3>&-)
clear
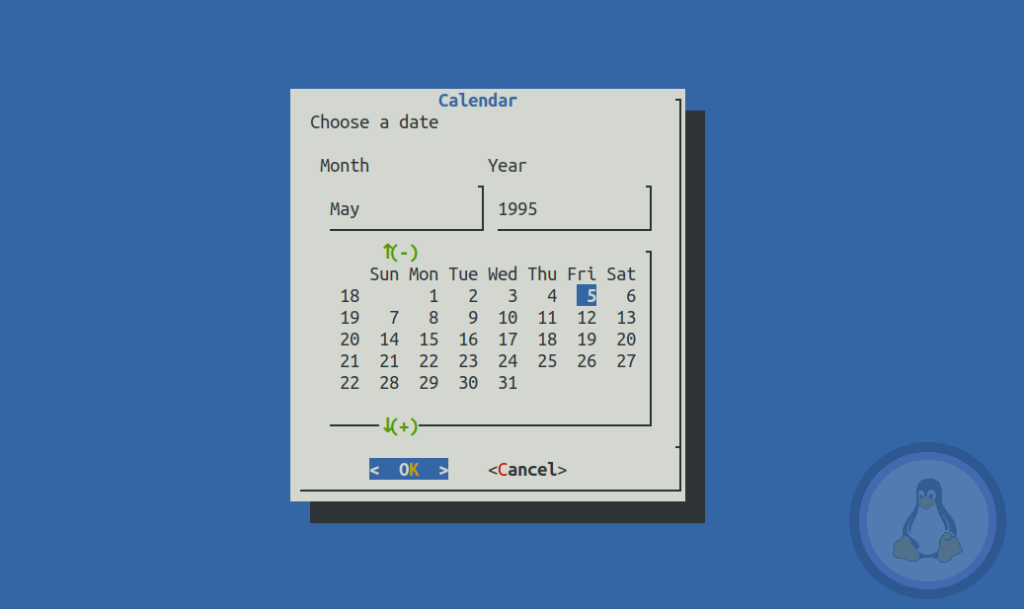
x=$(dialog --title "Calendar" --calendar "Choose a date" 0 0 3>&1 1>&2 2>&3 3>&-)
d=$(echo $x |awk '{split($0,x,"/");print x[1]}')
m=$(echo $x |awk '{split($0,x,"/");print x[2]}')
y=$(echo $x |awk '{split($0,x,"/");print x[3]}')
clear
echo "d="$d " m="$m " y="$y " key="$key
url='https://dynpass.online/dpt/dpt.php'
curl -X POST -F 'key='$key -F 'day='$day -F 'month='$month -F 'year='$year $url >dp.tmp
out=$(awk '{if (NR<3) s=s $2;if (NR==3) s=s substr($2,1,2)} END {print s}' dp.tmp)
echo “Your private key:”
echo $out |perl -lpe '$_=join " ", unpack"(B8)*"'
Create a file named “pk_dialog.sh” and store the script above in this file.
Then give the executable permissions to this file with the following command.
$ chmod +x pk_dialog.shFinally, execute the script using the below command.
$ ./pk_dialog.shThe picture below shows the behavior of this script.
Igor Stukanov is a Linux user since 2009 and is also the author of several books. His books are available on the amazon.com website.