If you have a website that provides downloadable materials like movies, games, etc., or a streaming website, then you need to limit your HTTP bandwidth RIGHT NOW.
Other users can also follow this guide to take the edge off common web attacks like DDOS or save your hosting provider’s bandwidth cap to ensure all the users have a good user experience.
In this beginner-friendly article, you will learn how to limit the network bandwidth (or you can say, restricting download speed) for the NGINX web server.
Table of Contents
Limiting the HTTP Bandwidth in NGINX
First, open your NGINX configuration file using your choice of text editor.
$ sudo vim /etc/nginx/nginx.confIf you are using a separate virtual host for your site, then specify the location of that site configuration file, which in most cases is located at /etc/nginx/sites-enabled/example.conf.
limit_rate
Then inside the configuration file, you need to use the limit_rate directive, which limits the rate of response transmission to a client.
The rate limit can be specified in bytes per second by default, m for megabytes, and g for gigabytes.
limit_rate 20k;If you specify the parameter value to zero value then it will disable the rate limiting.
Other than that you specify this directive within the location {}, server {}, and http {} contexts.
limit_rate_after
One more thing to note is that the above-mentioned directive will limit access to all methods except GET and HEAD.
However, you can use the limit_rate_after directive to impose the limit after the client downloaded a certain amount of data.
limit_rate_after 500k;During this time, users are allowed to quickly download a certain amount of data like a file header or file index after which the further transmission of a response to a client will be rate limited.
Similar to limit_rate directive it is also valid for the location {}, server {}, and http {} contexts.
Restrict Multiple Connections
The above two methods will limit the client’s rate of response transmission after the limit_rate_after value reaches its final point.
But in this case, the limit is set to per request, meaning that if the client tries to open multiple or several connections simultaneously, then the overall rate will be twice as much as the specified limit.
To prevent it from happening, you can use the shared memory to limit the connections per client using a parameter like a client’s IP address.
So we will use the limit_conn_zone directive in the HTTP block to limit the total amount of shared memory available for managing connections.
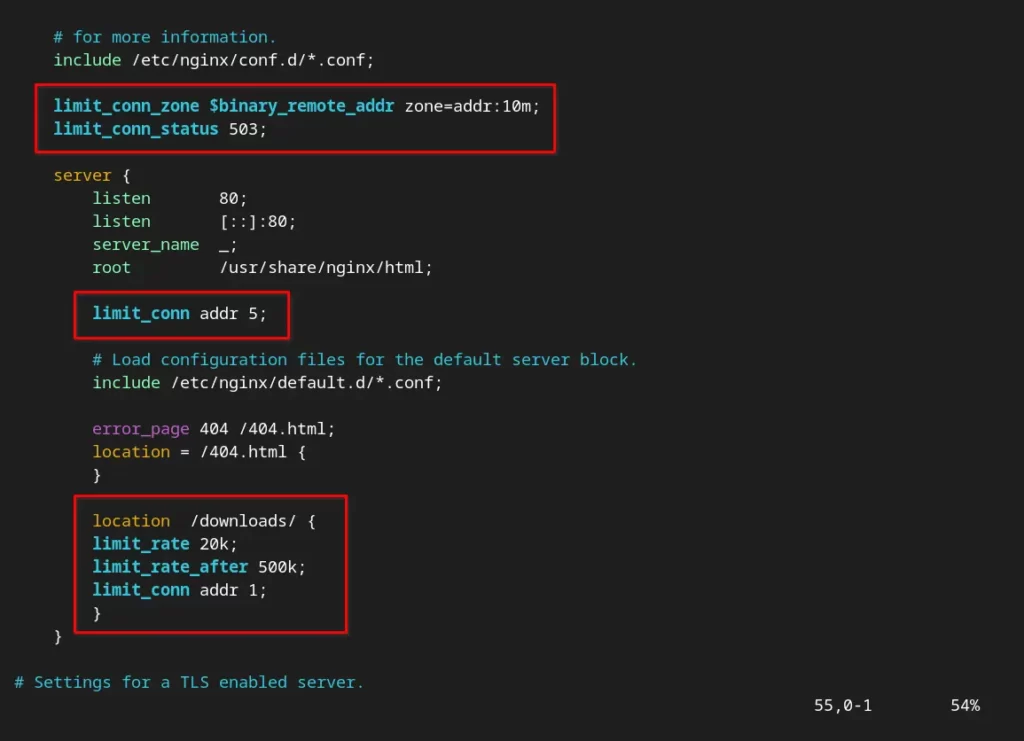
limit_conn_zone $binary_remote_addr zone=addr:10m;After that, you need to add the following line to block the limit of five connections per IP address.
limit_conn addr 5;Note that the above settings will be affected if more than 5 users share the same IP address behind the NAT devices.
After applying all the above-mentioned directives, your NGINX configuration file should look like the one below.
Limiting the HTTP Bandwidth Dynamically in NGINX
For the limit_rate directive parameter, you can specify its value dynamically depending upon certain conditions.
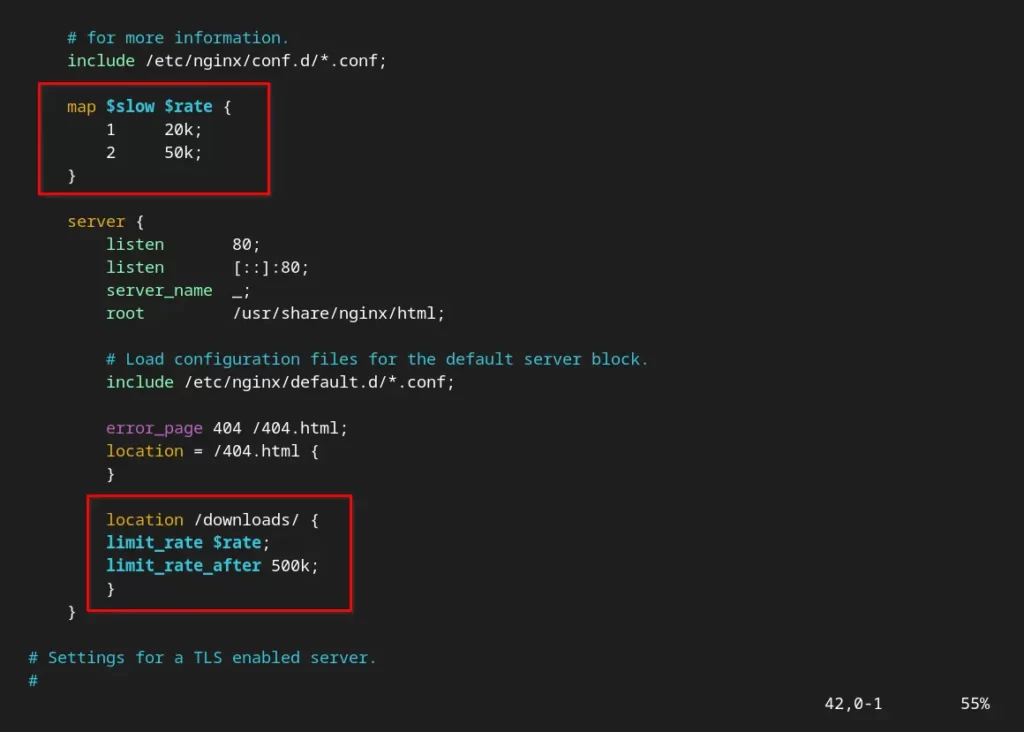
Below we are using the map block which enables you to create a new variable whose value can be used with the if statement (we will not cover the if statement examples if you want then let us know in the comment section).
map $slow $rate {
1 20k;
2 50k;
}
limit_rate $rate;Below is the output of your NGINX configuration file after the changes are applied.
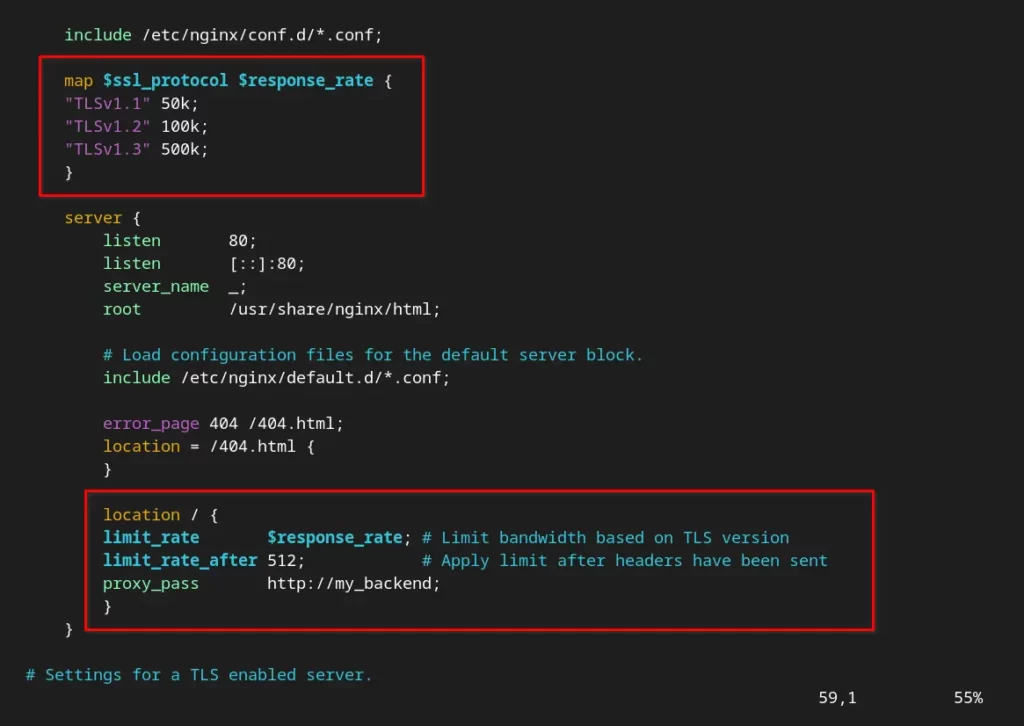
Here is another example, which will dynamically limit the HTTP bandwidth based on the TLS version, for example, allowing a higher bandwidth limit for modern browsers.
map $ssl_protocol $response_rate {
"TLSv1.1" 50k;
"TLSv1.2" 100k;
"TLSv1.3" 500k;
}Below is the output of the NGINX configuration file after the implementation.
That’s all you require to limit/prevent/block the HTTP/network bandwidth in NGINX.
Below are some useful links for you.
- How to Increase NGINX Worker Connections Limit in Linux
- How to Limit the Number of Connections in NGINX
- How to Limit the Rate of Connections in NGINX
If you have any queries or questions regarding this topic, then feel free to ask us in the comment section.

Innovative tech mind with 12 years of experience working as a computer programmer, web developer, and security researcher. Capable of working with a variety of technology and software solutions, and managing databases.