The su (aka substitute user) command is used by Linux users to transition from the current user to another user or super user (root account) without changing the current working directory or user environment.
A standard user with sudo access has extra privileges while using the su command. For instance, if a user with sudo access uses the su command to try to switch to the root account, they are required to supply their own password.

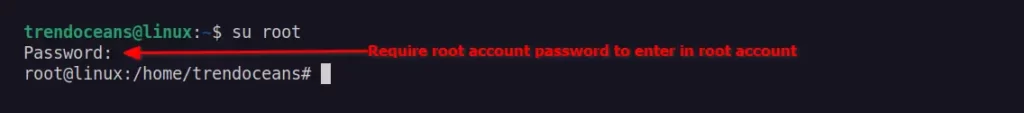
However, users who don’t have access to sudo try to switch to the root account using the su command. They are required to provide a root account password.
What do you think? Which one is way more secure to prevent unnecessary access to root or any other account? No doubt, the second option is secure and recommended unless you own the system, trust the user, or are using your own personal desktop.
As a system administrator, you have access to revoke su permission for a user or group of users from the sudoers file. The sudoers file is used to control and manage a user’s sudo privileges.
By default, the location for the sudoers file is at /etc/sudoers, but it is recommended to edit the file using the sudo visudo command.
Let’s stop this talk and get to the real meat by learning how to disable su for sudo users and groups of users in Linux.
Revoke su Access for a Sudo User
First, you should always take a backup of the sudo configuration file before making any changes. Execute the following command to take a backup of the sudoers file.
$ sudo cp /etc/sudoers /etc/sudoers.bakThen open your visudo configuration file by issuing the following command.
# Execute below command if you logged as super user
$ visudo
# Execute below command if you are a normal user with sudo privileges
$ sudo visudoBelow is the output of the above command.
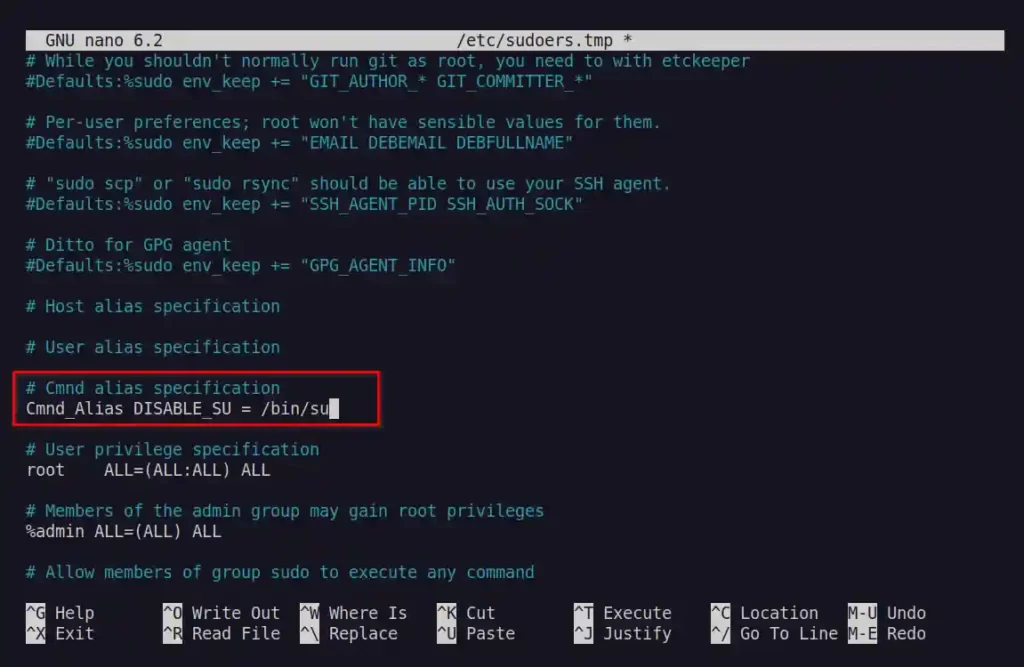
In the next step, you need to create the following alias under the comment section “Cmnd alias specification“.
Cmnd_Alias DISABLE_SU = /bin/suBelow is the output of the above command.
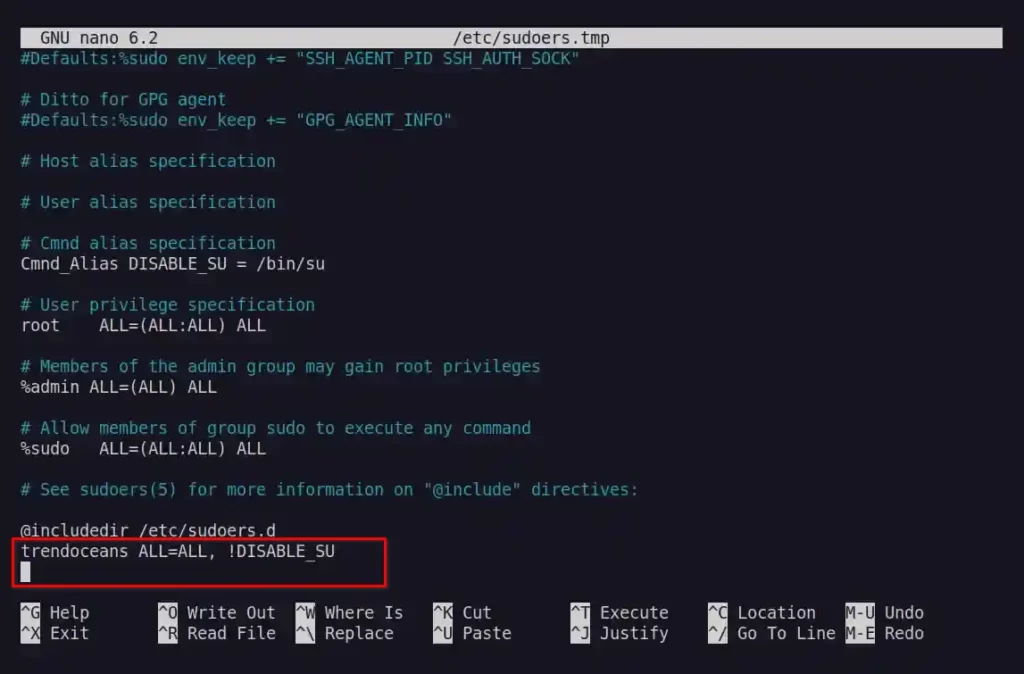
Then add the following line by replacing “trendoceans” with the actual user at the end of the sudoers file.
trendoceans ALL=ALL, !DISABLE_SUBelow is the output of the above command.
Save/close the file and restart your terminal session.
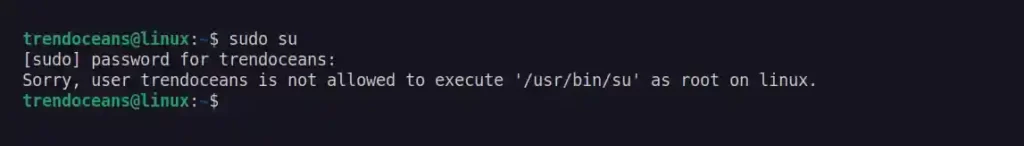
To verify the changes are made properly, open a new terminal session and execute the sudo su command. The system should return an error with the message “Sorry, user trendoceans is not allowed to execute '/usr/bin/su' as root on linux.“, as shown below.
$ sudo suBelow is the output of the above command.
Revoke su Access for a Group of Sudo Users
By using the same DISABLE_SU variable, you can prevent a group of sudo users from accessing the su command. For example, in the sudoers file, you will find an admin group.
Let’s see, how you can prevent the user added to the admin group from accessing the su command. For that, replace the below line.
%admin ALL=(ALL) ALLto this.
%admin ALL=(ALL) ALL, !DISABLE_SUIn the sudoers file and then, save and close the file.
Lastly, add the user to the admin group by using the following command.
$ sudo usermod -aG admin trendoceansDo not forget to replace “trendoceans” with the actual user. Now if the users try to access su from the sudo command, they will get the same error with the message “Sorry, user trendoceans is not allowed to execute '/usr/bin/su' as root on linux.“.
That’s all for now. If you found this article useful and want to know more about different ways to restrict user access in Linux systems, then let us know in the comment section.
I do not see the point of running ‘sudo su’ in the first place since there are plenty of other ways to get obtain with sudo. The easiest is ‘sudo -i’ but ‘sudo /bin/sh’ or any other shell would work fine. It is not even realistic to disable all shell programs manually since users can copy the executable somewhere else.
Simply speaking, if ALL is in the program list then the user can do everything he wants.
The ! operator only makes sense if the user already has limited access and you want to restrict him even more. For example, allow john to execute everything in /usr/sbin except for /usr/sbin/foobar:
john ALL = /usr/sbin/ , !/usr/sbin/foobar
Absolutely correct! Maybe try SELinux or something