Want to install the Metasploit Framework on Linux? Look no further! Follow these simple steps to get started:
The Rapid7-powered Metasploit Framework is the world’s leading penetration testing framework. The Project is a collaboration between the open-source community and Rapid7 to provide a tool for developing and executing exploit code against a target machine.
Also Read: How to Install Metasploit Framework with GUI Method on Linux
It is mostly known for:
- Write, test, and execute exploit code
- Intrusion Detection System (IDS) signature development
- Vulnerability Assessment and Pentesting
- Test security vulnerabilities, enumerate networks, execute attacks, and evade detection.
H. D. Moore created Metasploit in 2003 as a portable network tool using Perl. By 2007, the Metasploit Framework had been completely rewritten in Ruby. On October 21, 2009, the Metasploit Project announced that it had been acquired by Rapid7, a security company that provides unified vulnerability management solutions.
By default, Kali Linux and Parrot OS provide the Metasploit Framework within their operating systems. Even other distributions such as Debian, Ubuntu, Fedora, AlmaLinux, Manjaro, etc., can easily install it on their systems.

Table of Contents
How to Install Metasploit Framework on Linux via Terminal
To install Metasploit Framework on your system, you need to have a curl package (a command-line tool that enables data transfer over various network protocols) installed. That can be done using any of the below commands depending upon your Linux distribution.
$ sudo apt install curl # Installing curl for Debian, Ubuntu, Linux Mint, Pop!_os
$ sudo dnf install curl # Installing curl for Arch, Manjaro, EndeavorOS
$ sudo pacman -Sy curl # Installing curl for RHEL, Fedora, Alma LinuxNow, you can easily install the Metasploit Framework package and add the build repository to your system via terminal using the following command.
$ curl https://raw.githubusercontent.com/rapid7/metasploit-omnibus/master/config/templates/metasploit-framework-wrappers/msfupdate.erb > msfinstall && chmod 755 msfinstall && ./msfinstallBelow is the output of the above command.
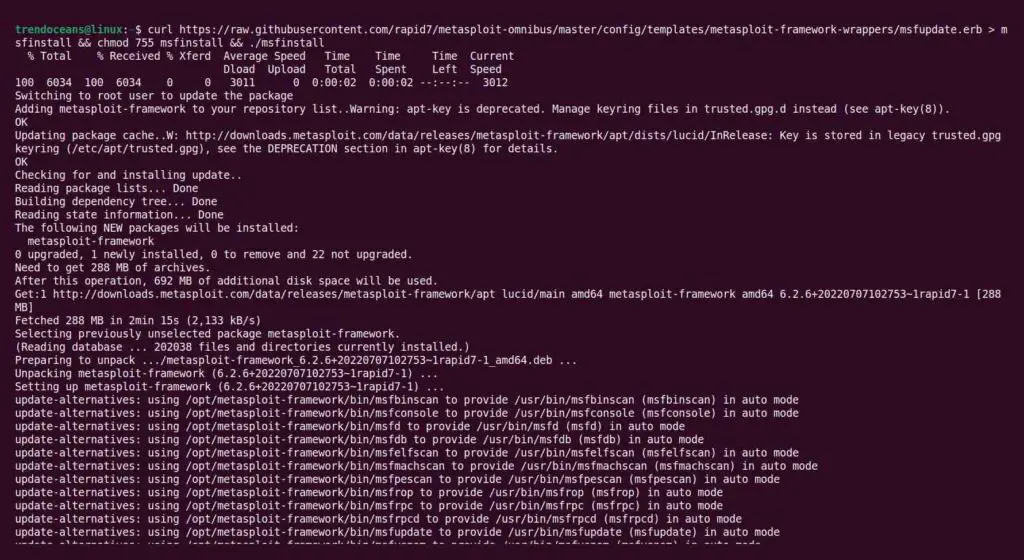
After the installation is successfully completed, open your terminal and execute the following command to start the msfconsole.
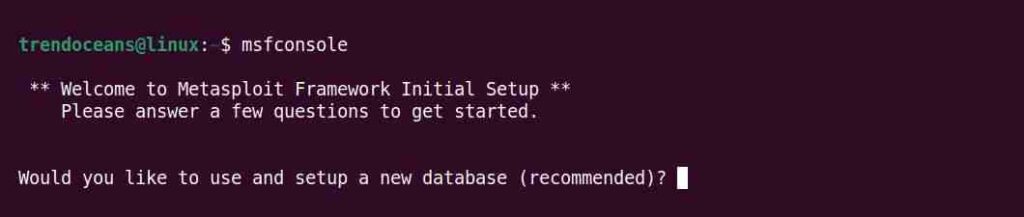
$ msfconsoleFor a fresh installation, it will ask you to set up a new database.
Type “y” for “yes” to run the initial configuration script to create the initial database.
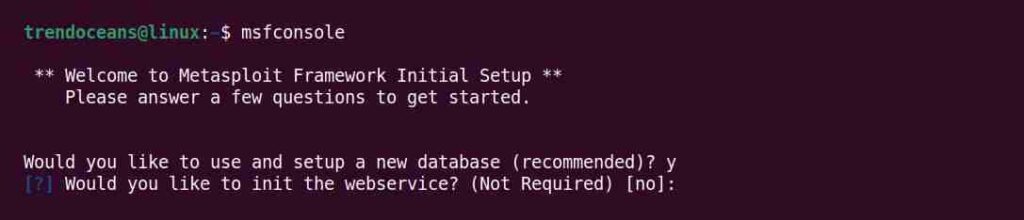
Next, it will ask you to set up web services for APIs that may rarely be of any use to you.
Type “n” or “no“.
If all goes well, you will be presented with the Metasploit console as shown below.
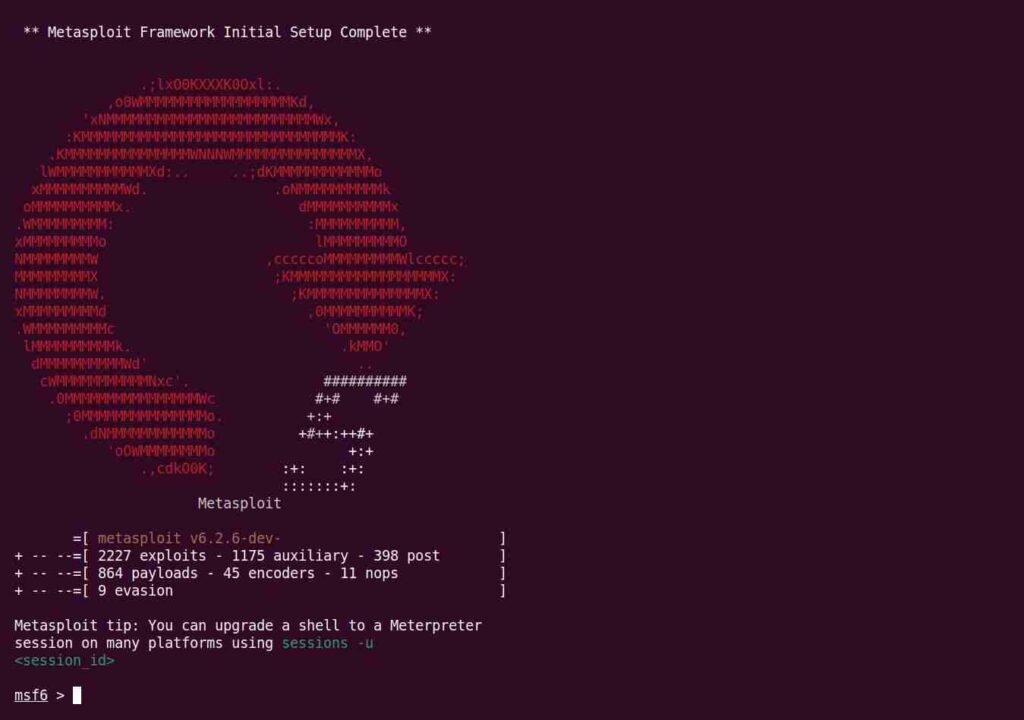
Run the following command in the Metasploit console to make sure the database is up and running.
$ db_statusIf the Metasploit Framework successfully connects to the database, the following status will display:
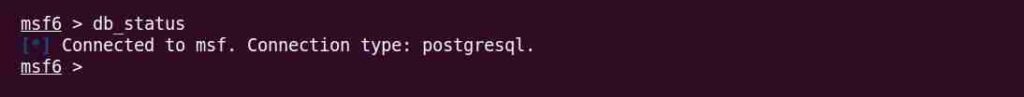
In case the database failed to initialize, run the following command outside the Metasploit console.
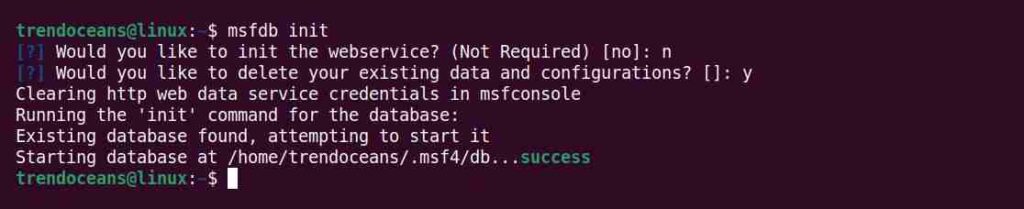
$ msfdb initIt will ask you to initialize the web service; type “n” or “no“, and then to delete your existing data and configuration, type “y” or “yes“, as shown below.
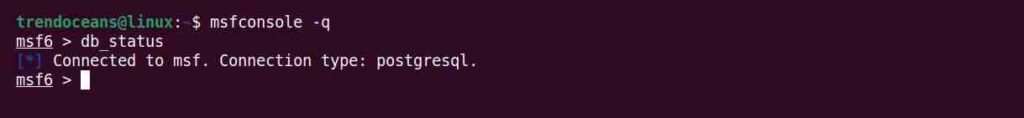
Now that the PostgreSQL service is up and running and the database is initialized, you can launch msfconsole and verify database connectivity with the db_status command as shown below.
List of Metasploit Command
After the database starts, you can use any of the following commands to manage the database:
| Commands | Usage |
msfdb reinit | To delete and reinitialize the database |
msfdb delete | To delete the database |
msfdb start | To start the database |
msfdb stop | To stop the database |
msfdb status | Shows the database status |
Common Commands Used with msfconsole.
| Commands | Usage |
help | To list all the options available in msfconsole |
| You can prepend help to any command to see a list of available options |
search name:mysql | To search modules using a descriptive name |
use [MODULE] | Will change your context to a specific module, exposing type-specific commands |
show exploits | To get a listing of all exploits contained in the framework |
show payloads | Display the payloads that are compatible with that particular exploit |
info [EXPLOIT NAME] | Shows detailed information about a particular module including all options, targets, and other information |
use [EXPLOIT] | Will change your context to a specific module, exposing type-specific commands |
show options | Display which settings are available and/or required for that specific module |
set [PAYLOAD] | Allows you to set the specific payload for your exploit |
show target | To see which targets are supported |
show advanced | To see more advanced options |
set RHOST [TARGET IP] | Allows you to configure Framework options and parameters for the current module you are working with |
set LHOST [TARGET IP] | Allows you to set up the localhost IP address for the reverse communications needed to open the reverse command shell |
connect [IP ADDRESS] | Connect to a remote host from within msfconsole the same as you would with Netcat or Telnet |
edit | Edit the specific exploit that you’re working on |
back | To move out of the current context |
jobs | List all the running modules in the background |
kill [PID] | Kill the specific jobs with the PID specified |
exit | Exit from msfconsole |
Uninstalling Metasploit from Linux
This article is incomplete without showing you Metasploit removal steps. It is recommended to take a backup of your project data that you may want to keep, like reports and host data, before uninstalling Metasploit.
Once you decide to remove it, open your terminal using a Ctrl+Alt+t keyboard shortcut and follow the below steps to remove Metasploit from your Linux systems.
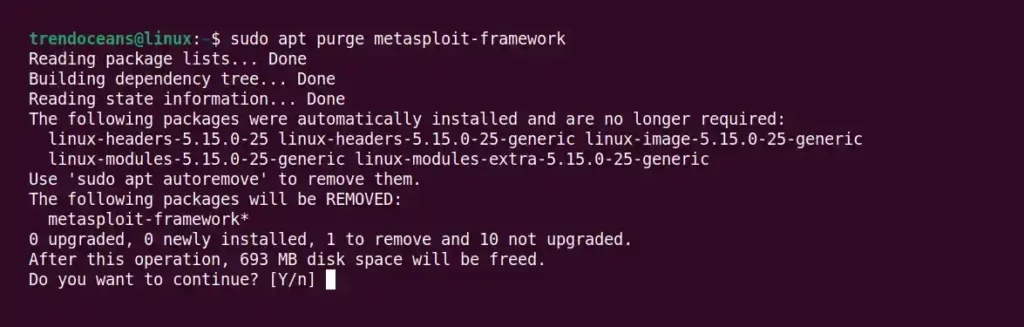
$ sudo apt purge metasploit-frameworkPress ‘Y‘ and the above command will remove the Metasploit framework from your system, as shown below.
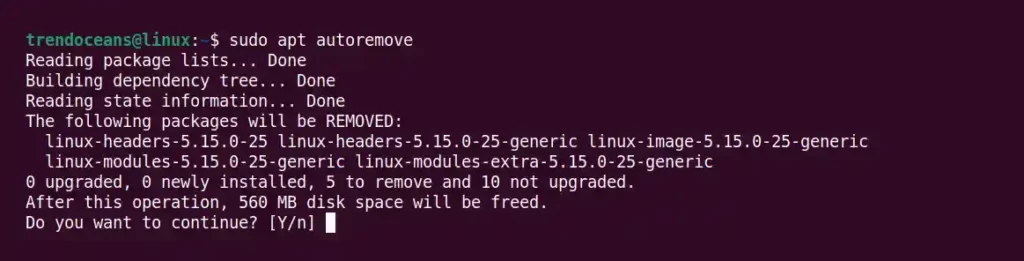
Lastly, execute the below command to remove the dependencies installed along with the Metasploit.
$ sudo apt autoremoveBelow is the output of the above command.
Wrap Up
The Metasploit Framework is a popular and well-known tool for penetration testers. If you are interested in learning more, then visit the Offensive Security website to get free documentation on different usages of the msfconsole command.
That’s all for now. For any queries or questions, feel free to ask in the comment section.

Innovative tech mind with 12 years of experience working as a computer programmer, web developer, and security researcher. Capable of working with a variety of technology and software solutions, and managing databases.