Proxychains is a UNIX/LINUX program that can redirect all your connection through a secure tunnel. Supported protocols used by proxychains are SOCKS4, SOCKS5, HTTP, and HTTPS.
To use proxychains, you can use Tor nodes (required to install the Tor command in your system). Or you can use separate SOCKS4/5 or HTTP/HTTPS protocols.
The proxy and VPN both helps to access the internet anonymously. While proxy usually uses the standard HTTP protocol and VPN encrypt data to ensure the safety of the connection.
Today you will learn to set up proxychains with the Tor network to tunnel all programs and commands through the Tor nodes.
Table of Contents
Install Tor
Tor is an onion router, generally referred to as Tor nodes. To connect with this Tor node require a command-line package or standalone browser.
It’s free and open-source, due to which countless applications like proxychains utilize its network to tunnel connection through the SOCKS5 protocol.
To install Tor enter the below command in your Linux terminal.
$ sudo apt install torStart Tor service in your system after the installation to use the SOCKS5 protocol inside proxychains.
$ sudo systemctl start torInstall Proxychains
It is time to install proxychains; it is available to install in all Linux distributions. To install, type or copy the below command in your Linux terminal.
$ sudo apt install proxychainsBefore we proxify commands or applications, we need to configure some settings from “/etc/proxychains.conf”.
Proxychains have three types of chains. Inside the configuration file, you need to configure which one to use to proxify your applications.
Note: Chains are referred to a list of proxies. Tor uses 3-4 proxy in order to tunnel all of the connection. You can rearranges the way your connection is made to the destination server using this three chains.
Dynamic Chains
All proxies are chained with each other. The dead proxies can be skipped required to have only one proxy alive to make the connection successful.
Tips: This chain is used to have a reliable connection while being anonymous.
Strict Chains
In this case, all proxies should be up and running in the series of orders they appear in the list of proxychains.
Tips: If you are strict about your privacy and don’t tolerate any leak, go ahead.
Random Chains
The connection will not be in series. The down proxy can be skipped, required to have at least one proxy up and running.
Tips: Random connections are good to have reliable connections. They are suggested for beginners.
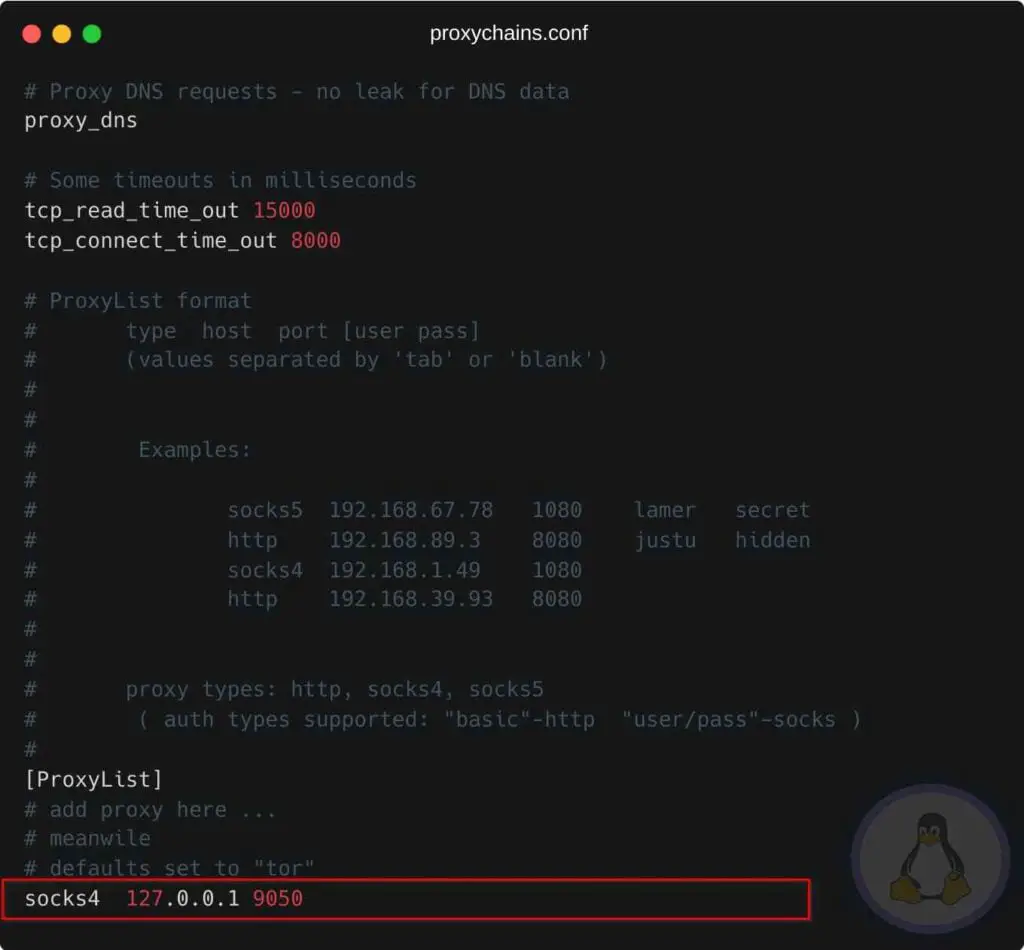
Next, you need to specify which chains you want to use in “proxychains.conf”, and add Tor socks. Edit “proxychains.conf” using your favorite TextEditor and make the below changes.
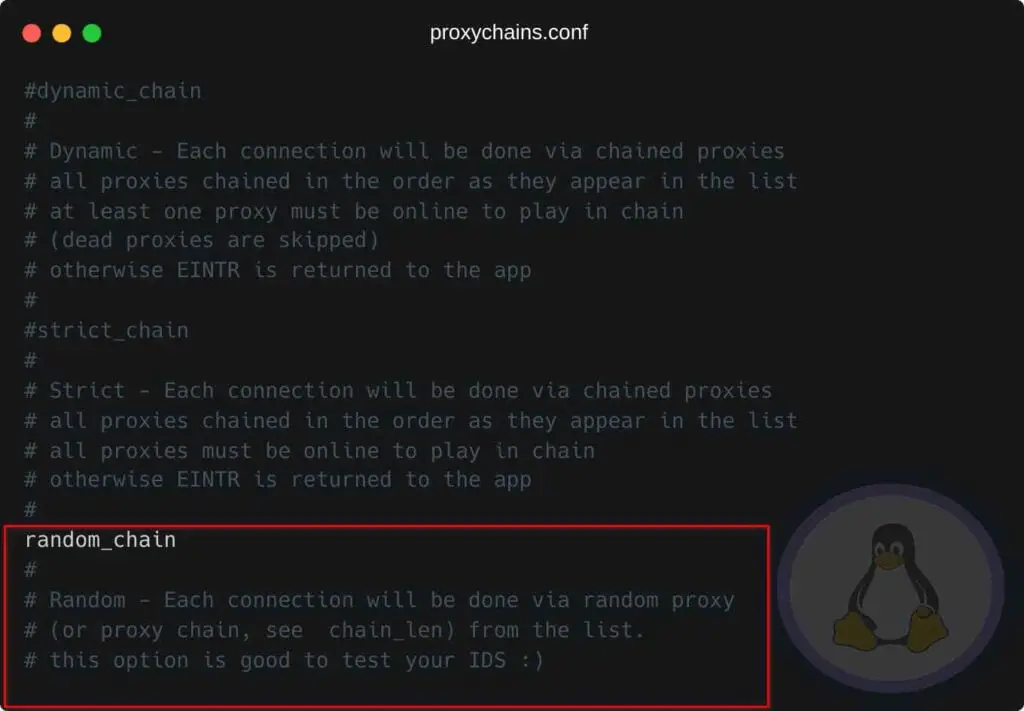
For the time being, we were heading with random_chains. You can choose wisely depending upon your needs and situation.
Next, you must specify the below lines at the end of the proxychains.conf.
socks4 127.0.0.1 9050
Restart your Tor service to ensure all the changes reflect properly using the below command.
$ sudo systemctl restart torProxify GUI applications
GUI applications like browsers and thunderbird can be easily redirected to the Tor socks network. To do so, you need to use the program name along with "proxychains".
Let us proxy google chrome using proxychains.
$ proxychains google-chromeProxify GUI Commands
Commands are the main cause to use proxychains, and you can easily pipe any connections through tor tunnel-like shown below.
$ proxychains curl ipinfo.io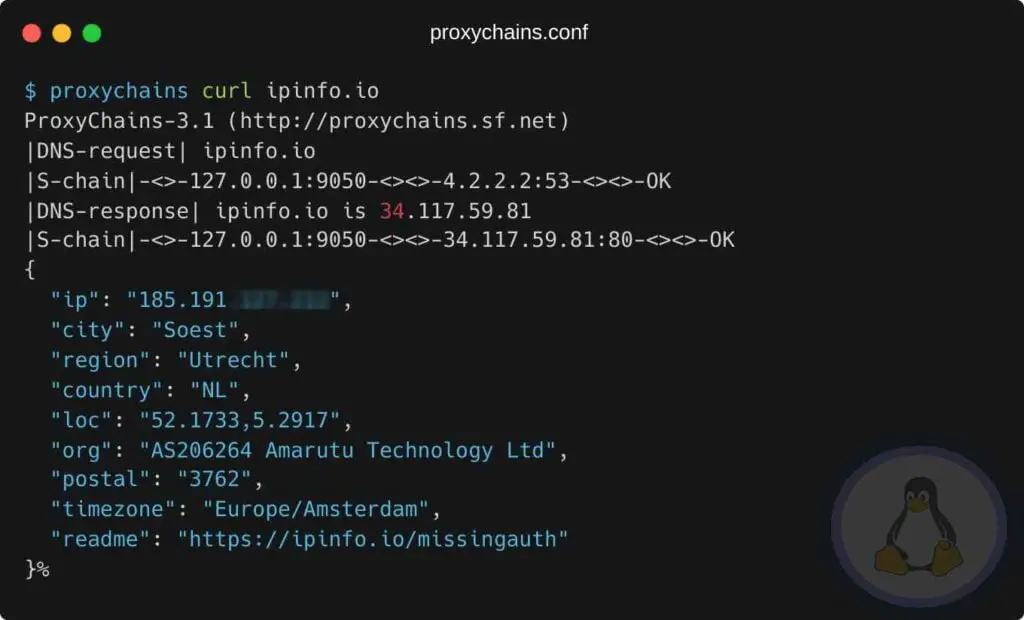
Final Thought
A VPN is more secure and encrypts all your network traffic, while a proxy works on an application level. They both help to anonymize, but only a VPN redirects your data packets through an encrypted tunnel. A proxy is more suitable for browsing the internet, but it’s not as safe and secure as a VPN.
If you have any questions, let us know in the comment section.

Innovative tech mind with 12 years of experience working as a computer programmer, web developer, and security researcher. Capable of working with a variety of technology and software solutions, and managing databases.