This guide will be focused on the installation of Tor Browser on the Linux system, with steps required to ensure your privacy and security.
At the time of the Facebook–Cambridge Analytica data scandal, people were amazed by the amount of their data on hand by these big giant companies. Even Edward Snowden had disclosed sensitive data the US government held on its citizens in the name of the project PRISM.
All of this data is gathered by the public (it’s you), posting all your private information on the social media feeds and sharing every event on your timeline. It might seem unharmful, but can create a good profile to target you for advertising, exploiting, and tracking.
To be apart from this ecosystem of privacy exploitation, you can have a VPN, which costs you some bucks. But what if I tell you there is a free and open-source privacy-centric browser that tunnels your data on nodes run by the volunteers?
What is the Tor Browser?
Tor Browser is currently the most trusted and secure browser to protect you from internet censorship and protect your data with the layer of nodes (also known as the onion routers) to make it harder for companies to track back to you.
It is available for Linux and macOS, although it is also available for Windows and Android (I am strongly against it). If you are using a Windows operating system, then I suggest creating a persistent Tails bootable USB.
How to Install the Tor Browser on Linux
Tor Browser is famous for providing privacy and security to its users while aligning with Linux ideology, which makes it harder for Linux distributions to avoid including it in their official repository.
Note: Do not skip the rest of the article after learning the installation steps. Otherwise, a small mistake can make you clearly visible among the crowd.
Install Tor Browser from the Distribution Repository
If you are using one of the Debian-based distributions such as Ubuntu, Pop!_OS, Linux Mint, Kali Linux, Parrot, etc. then the default apt package manager is enough to install it on your system using the following command.
$ sudo apt install torbrowser-launcherArch-based distributions such as Manjaro, Garuda, EndeavourOS, etc. can also use the default pacman package manager to install it on their system.
$ sudo pacman -Sy torbrowser-launcher Sadly, RHEL, Fedora, and CentOS users have to go through some extra steps in order to install it using the compressed file on their system.
Install Tor Browser on Any Linux Distribution
Visit the official Tor website to download the latest version of the compressed file. However, you can also use the wget command to download the Tor Browser v11.0.15 compressed file from your terminal using the following command.
Note: Downloading Tor Browser from the below command will download the current latest version (v11.0.15), which might change in the next few days.
$ wget https://www.torproject.org/dist/torbrowser/11.0.15/tor-browser-linux64-11.0.15_en-US.tar.xzAfter the compressed file is downloaded extract the content of the file and move into the directory using the following command.
$ tar xf ./tor-browser-linux64-11.0.15_en-US.tar.xz && cd tor-browser_en-US/Now you are ready to run the Tor Browser application using the following command.
$ ./start-tor-browser.desktopIf you have Flatpak installed and configured on your system, then you can easily download and install the Tor browser from Flathub. However, I do not recommend installing it due to the slow release and giving unnecessary disk space.
How to Run the Tor Browser on Linux
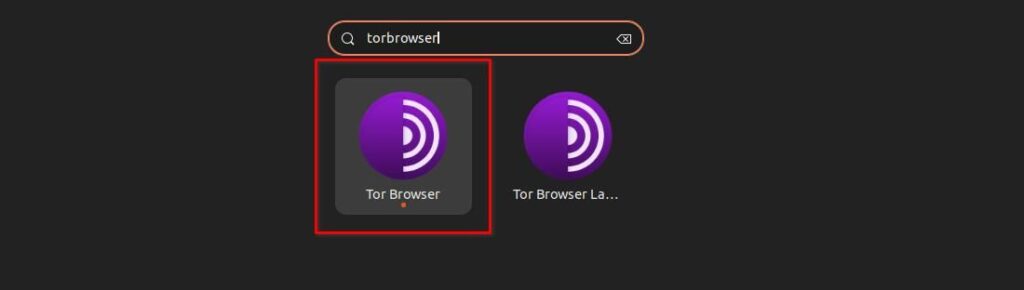
Once you have installed the Tor Browser on your Linux system. Execute the torbrowser-launcher command from your terminal app or search for the application from your system menu.
While searching for the application, you might find two entries. Leave the other one and just click on the Tor Browser inside the red square.
If you arefacing any errors, check the below FAQ to resolve them.
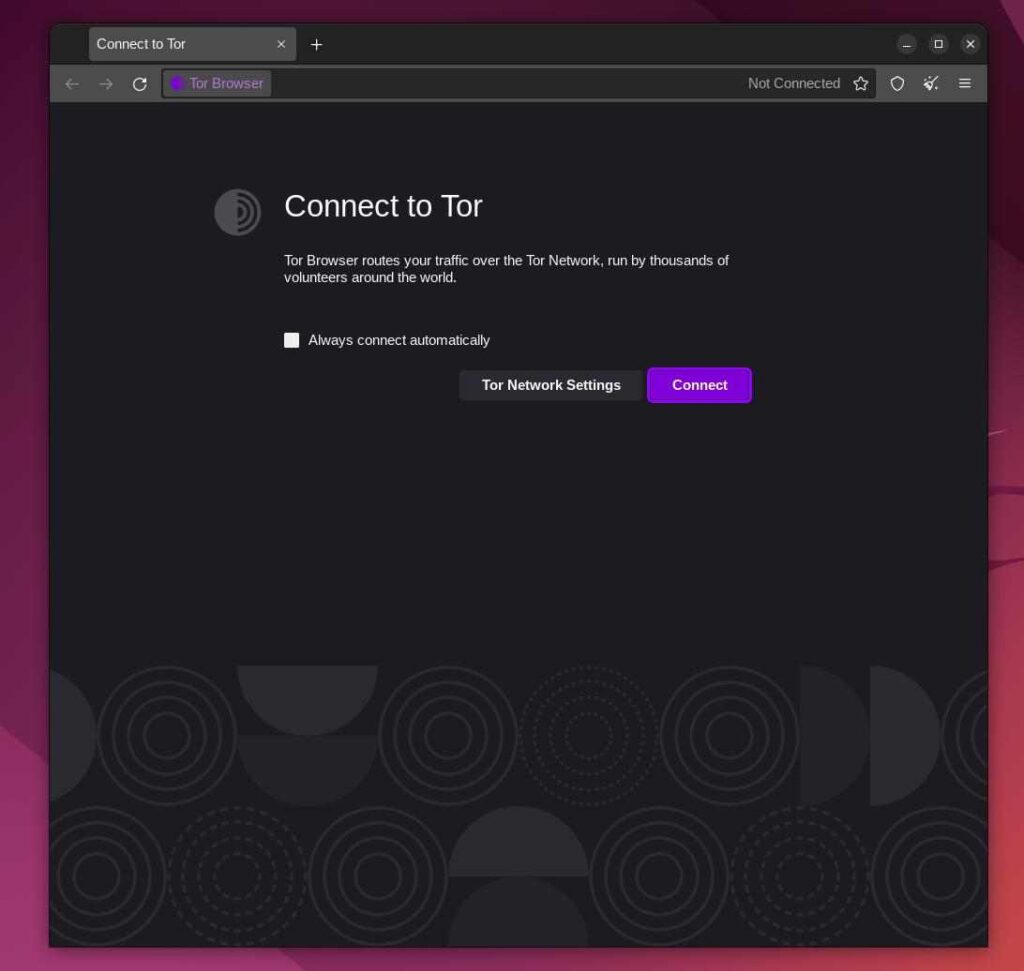
It will open the Tor Browser, as shown below.
Do not search for anything. Right now, the Tor Browser is not connected to the Tor Network (used with the Tor Browser to tunnel the traffic).
Select the Always connect automatically check box to let the Tor Browser automatically get connected to the Tor Network whenever the browser opens and then press the Connect button.
Also Read: How to Install Privacy-friendly Whatsapp Alternative Signal in Linux
After waiting for a few seconds, it gets connected to the Tor Network, having as its default search engine DuckDuckGo.
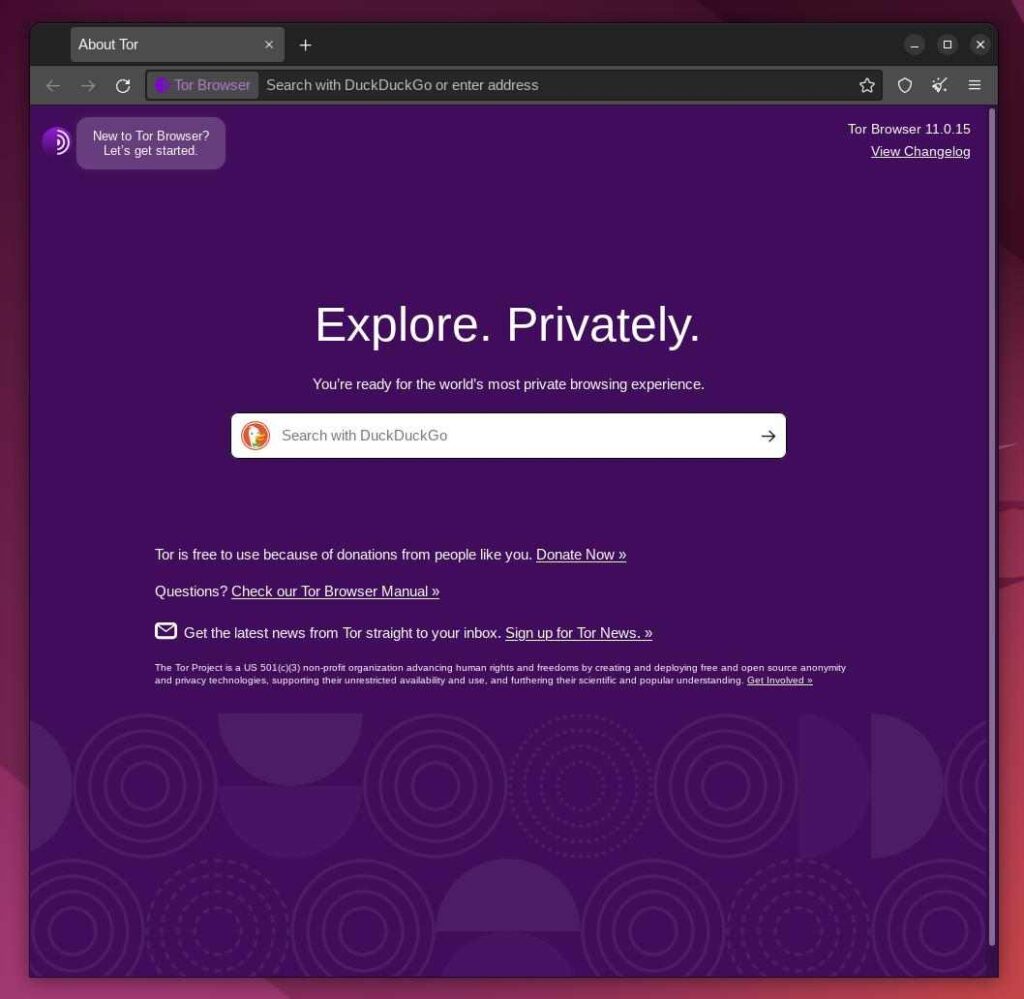
Finally, you are ready to surf the internet anonymously using the Tor Browser. However, the Tor Browser is bundled with several security extensions, such as HTTPS Everywhere (used to switch from the HTTP to HTTPS protocol) and NoScript (used to disable website javascript).
In the next part, we will discuss how to remove the Tor Browser. If you’re not interested, you can skip the part, but don’t skip the FAQ.
How to Remove Tor Browser on Linux
If you are done with the privacy stuff, do not hesitate to openly search for your queries on Google from a Chrome, Firefox, or Vivaldi browser. Then the Tor Browser was not created for you. To remove it, simply execute the below command depending on the method you used to install it.
Also Read: Proxychains – Run Commands and Applications using Proxy Tunnels
$ sudo apt remove torbrowser-launcher #Remove from Ubuntu, Pop!_OS, Linux Mint, etc
$ sudo pacman -Rs torbrowser-launcher #Remove from Manjaro, Garuda, EndeavourOS, etcIf you were using the compressed version of Tor Browser, deleting the directory is enough.
FAQ and Security Tips
It’s possible that you face a “SIGNATURE VERIFICATION FAILED” error with the error code “GENERIC_VERIFY_FAIL” while installing Tor Browser from the APT package packager. The reason is the outdated GPG key used for verifying the torbrowser-launcher that can be refreshed using the gpg --homedir "$HOME/.local/share/torbrowser/gnupg_homedir" --refresh-keys --keyserver keyserver.ubuntu.com command.
If you are not an expert in command, then it is not recommended to use a VPN along with the Tor network.
The Tor Network consists of thousands of onion routers (also known as Tor Nodes) to prevent your location from being exposed by providing you with multiple layers of masks.
The circuit is the currently active series of Tor Nodes that your Tor Browser is using to bounce your traffic from one location to another.
It is forbidden to maximize the Tor Browser Window to prevent the site from accessing your system screen size and resolution.
By default, Tor Browser chooses the standard security level to provide you privacy with speed. However, you can switch to a safer or safest level in exchange for browsing speed.
I suggest you to avoid Google search for your queries and switch to more privacy-oriented search engines such as DuckDuckGo.
You can visit any site from the Tor Browser until it is legal. However, many sites provide their own onion version that I recommend you use to put a cherry on your privacy.
Obviously, the answer is yes. However, I suggest you to avoid such sites, especially if you are unfamiliar with the technical stuff.
This is the most debatable question. The answer is yes, if you are a normal user who just wants to protect your data from social giants and maintain good privacy on the internet. However, fraudsters and people with unethical activities can be caught by monitoring them and creating logs of activity to precisely find the location of the culprit. In the past, many people doing unethical activities have been caught by the security agency. So, use it only to protect your privacy, not for any other purpose.
Wrap Up
So, if you are a student, teacher, journalist, activist, etc., who wants to protect your privacy from the sharks of the internet. Then Tor Browser can be your life saviour.
If you have any questions or queries, then the comments section is always open for you.
I really liked your site. Thanks for the information.